
Nice neighbourhood, https://www.amsterdam.nl...
For your copy and paste pleasure:
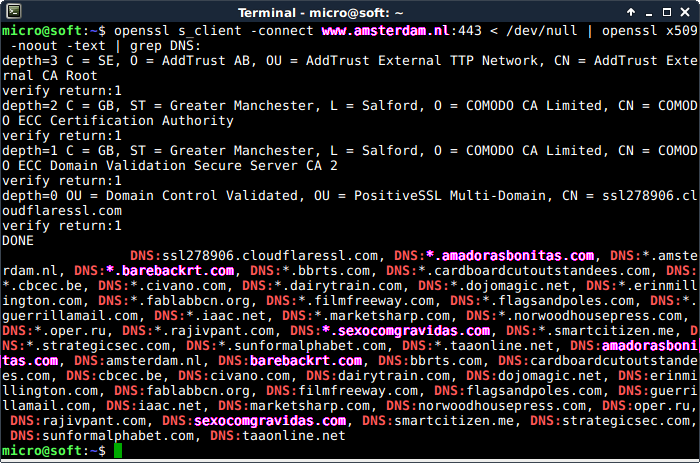
openssl s_client -connect www.amsterdam.nl:443 < /dev/null | openssl x509 -noout -text | grep DNS:
Update
03.11.18: Cloudflare fixed this mess somewhat. They now look for SNI servernames and use customer-specific certs. See:
openssl s_client -servername www.amsterdam.nl -connect www.amsterdam.nl:443 < /dev/null | openssl x509 -noout -text | grep DNS:
(notice the -servername in the above vs. the original command that will fail with something like
140246838507160:error:14077410:SSL routines:SSL23_GET_SERVER_HELLO:sslv3 alert handshake failure:s23_clnt.c:769: now)

Manually copying the BIND master zone configuration to slave servers is a tedious and error-prone process.
There are configuration management systems available for large deployments and BIND can support database backends as well which allow synchronization virtually behind the scenes.
For my use these options are overly complex and have unwanted risks associated with it.
The better option is to automate generating the BIND slave configuration from the BIND master named.conf.local.
Continue reading "Replicating BIND DNS slave configurations from BIND DNS master servers"


