Keeping IRC nicks active
Typical IRC services usually allow you to register with nickserv and link a number of nicks to a personal account. It's quite common to have nick, nick_ and nick__ as many IRC clients auto-append underscores if the primary nickname is already in use when connecting. Obviously you can set these alternate nicknames to almost anything you like in a decent client.
Some folks also group a "vanity" nickname or two for whatever reason. To keep these active, people do the "nick shuffle" (/nick newnick, /nick oldnick) all the time:
People who forget the occasional nick shuffle may end up losing a grouped nick because it became inactive. While freenode staff try to contact people before dropping linked nicks, there are occasional prunes of "old data" from the services database. And then nobody can really ask upfront.
So before the next big purge comes up, I wrote a small bash script that logs into a nickserv account and cycles through the linked nicks. A few friends and me have used it successfully for many months now.
Grab a copy of keepnick (2.4kB) and drop it into /usr/local/bin.
Keepnick expects to have an accountname, the corresponding password and then a sequence of linked nicks given on its command line.
Something like
should work.
For regular use, you need to set up a cron job to call keepnick e.g. every week. So put something like the following script into /etc/cron.weekly/keepnicks_irc or create a corresponding crontab entry for keepnicks_irc if you do not have the convenient cron.* directories set up:
#
# run keepnick for user(s) irc account(s)
# intended to be run from cron, e.g. through /etc/cron.weekly
#
KEEPNICK="/usr/local/bin/keepnick"
# better safe than sorry
PATH="/sbin:/bin:/usr/sbin:/usr/bin:/usr/local/bin"
export PATH
$KEEPNICK accountname1 passw0rd1 linked_nick1 linked_nick1_ linked_nick1__
$KEEPNICK accountname2 passw0rd2 linked_nick1 linked_nick2_ linked_nick2__
You should see keepnick in action now every week like this:
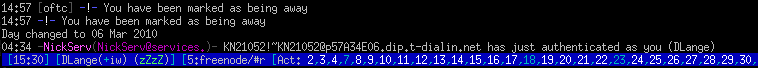
What happens here is that the IRC services package tells you, keepnick has just authenticated to your account and will now shuffle through all nicks you asked it to. The big advantage is that is does this outside of channels, so not annoying any users. The cron job should make sure you don't forget the nick shuffle anymore.
Making sure your bash supports network connections
Stock bash will support network connections but on Debian and old (=pre-karmic) Ubuntu that capability was disabled at compile time.
If you need to check whether your bash is compiled with network support, type cat < /dev/tcp/time.nist.gov/13 into a bash terminal.
In case that gives you a RFC-867 time string, you're all fine.
If not, re-compile your bash with --enable-net-redirections.
Now for something more advanced (but entirely optional):
Adding SSL
If you run keepnick from your desktop machine, there may not be much use in SSL. But if you want to run it off a laptop and that laptop may be connected to untrusted Wireless LAN at times, you should secure the communication via SSL. Enabling SSL means you need to:
- decide on how much SSL verification you want to do
- change the host in keepnick to localhost (as stunnel will SSLify a local loopback connection to a remote system specified in stunnel's config file)
- change the port in keepnick to the stunnel port (e.g. matching 7000 or 7070 as used for SSL on freenode)
- run stunnel to SSLify a local connection (e.g. from the cron script)
- run keepnick (from the cron script)
- (optionally) kill stunnel again after keepnick has run (e.g. from the cron script)
The first point is the crux most people forget about SSL. If you don't verify certificates, SSL is vulnerable to man-in-the-middle attacks.
So a sample stunnel configuration (/etc/stunnel/freenode.conf) looks like this:
# Basic stunnel configuration file for using freenode via SSL (port 7070)
# empty pid to disable pid creation
pid =
# Verification depth, 2 requires Gandi CA cert, 3 requires freenode cert
verify = 3
# where to find the CA freenode used (i.e. Gandi) - used for verify = 2
CApath = /etc/ssl/certs
# freenode's public cert used for ssl irc - used for verify = 3
CAfile = freenode_cert.pem
# Some debugging options useful for troubleshooting
#debug = 7
#output = stunnel.log
# We need to use client mode
client = yes
# Service-level configuration for freenode ssl irc
[freenode]
accept = localhost:7070
connect = chat.freenode.org:7070
verify = 2 (=verify peer certificate) means you need to have the CAcert freenode uses, see their SSL FAQ for a link.
Using this basically means you trust Gandi (which is the CA freenode uses at the time of writing). It does have the nice advantage of verifying every certificate offered as long as your local CA store (usually /etc/ssl/certs) contains a copy of the signing certificate. So if freenode updates their cert and you have the corresponding CAcert available locally (i.e. through your distribution), you're fine.
verify = 3 (=verify peer with locally installed certificate) means you have a copy of the public certificate from freenode SSL itself and match that to verify the connection. Using this basically means you trust freenode (which you obviously do to the point of using their service). Now their cert changes once a year (as that is how long most signed SSL certs last ... cough renewal fee cough) so this option will only work until freenode decides to update the cert. Well actually only the signature needed to be renewed on a longer lasting pubkey, but x509 ... ah well, that is a topic for an entirely different article.
You need to grab a copy of freenode's SSL cert and the excellent OpenSSL Command-Line How-to by Paul Heinlein contains a getcert script to help you do that. Copy it from the How-to and run:
Now cat certs.pem | openssl x509 -noout -subject -dates will show you something like:
subject= /OU=Domain Control Validated/OU=Gandi Standard Wildcard SSL/CN=*.freenode.net
notBefore=Jan 13 00:00:00 2010 GMT
notAfter=Jan 13 23:59:59 2011 GMT
So you should be safe until the end of the year.
Updates:
22.06.21 Freenode is dead, and people have mostly moved to Libera. So I updated the keepnick script to default to Libera.
12.01.14 To help you debug stunnel this may be helpful:
-d = local port to listen to (defaults to the specified port on all local IP addresses, you may want to use localhost:7070), -c = client mode, -f = foreground (no detaching), -P '' (two single quotes) = don't write pid file, -r = destination host to connect to
Once you have that running add -v 2 (or 3) as per the verify option discussion above.
05.04.12 The regular freenode user database pruning seems to come up again. Announced for ~May 2012, see freenode's staff blog entry by Martinp23.

Comments
Display comments as Linear | Threaded