Tales from the Edge. #Security.
Late 2017, King county, Washington
An overworked team with an impossible mission, to create a secure Internet browser, on Windows, is called to the weekly time-waster product team meeting.
Product Manager:
Team, you know that Edge needs to be the most secure browser on the planet, right?
So how can this thing segfault if some dude from the security consultancy fuzzes the Backup.dat?
You MUST make sure this is protected. It MUST be a violation of Windows Policy to modify the file. Go, make it happen! Report back next week!
The team disperses.
Early next morning, at a set of tables in the middle of a dimly lit cube farm...
Developer:
Hey, team lead, do you know what the PM meant with "Windows Policy"? I never heard about a "Windows Policy". Is this the "Group Policy"? Or did he mean the product license? Like the shrink-wrap contract? Do we need to consult legal?
Team lead:
Oh, ffs, Bob. No time for discussion. The requirement is crystal clear. Implement it. You're the security lead. We have a deadline approaching.
Developer:
O.k., boss. I'll see what I can do.
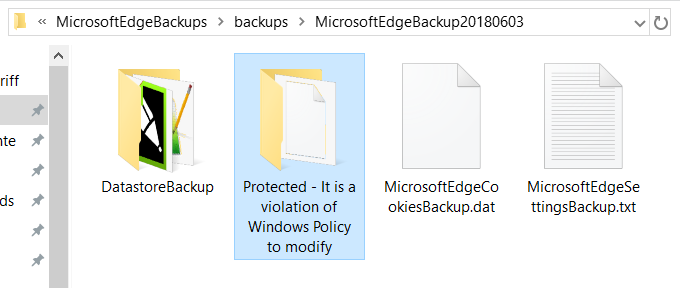
O Rly?
This is unfortunately not a joke. I found this in a Windows client backup log:
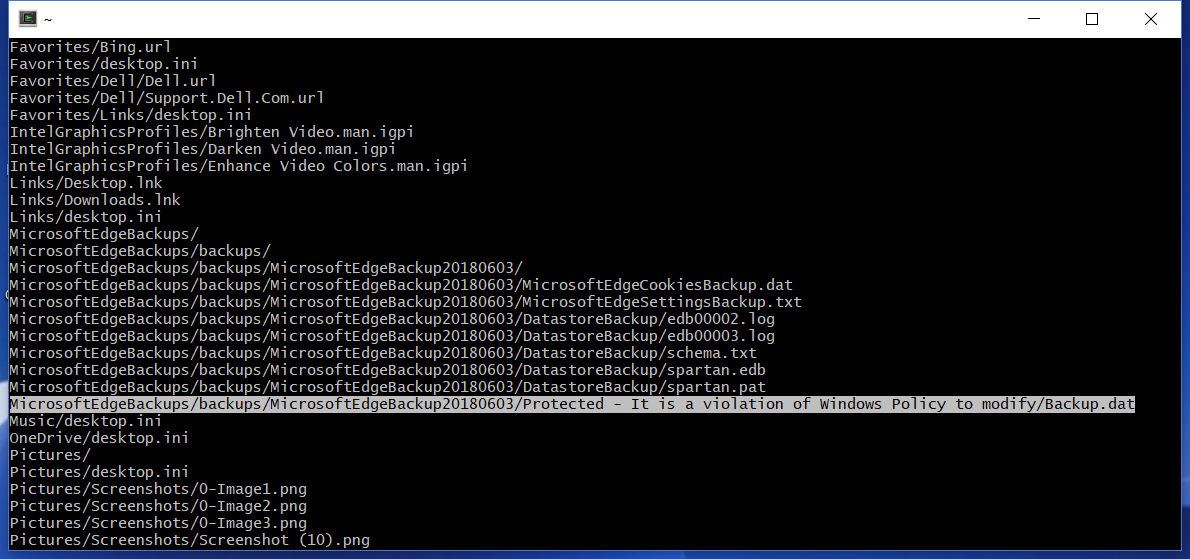
Others have wondered, too:
While you're at it, please admire the beauty of the URL. Underscores or dashes? Short slugs? Four Insiders? Let's tack a UUID on top, always good to have UUIDs! And NEWID is so easy to use in SQL Server. IDENTITY is two more keystrokes.
Next time, I'll do a piece on that bug report, how swearing at support people doesn't help and why an "Insider Preview" program is totally worth it ... if somebody were actually monitoring the feedback.
And why the second answer in that forum is better SEO than the work that went into the clean URL.
And why you have %LOCALAPPDATA% and still use the home directory to store browser cookie backup files in the first place.
...
Update:
15.02.19: Microsoft has decided to discontinue trying to develop a competitive browser engine for MS Edge and instead will re-base on Google Chromium. They have put up a Github repository with a README to explain their rationale.
13.06.18: Even the Windows registry has this security - ehem - feature applied:
Bookmarks in the registry. This gets better and better.
So "Windows policy" might be the "Microsoft browser extension policy"?
BTW: Found via https://answers.microsoft.com/en-us/windows/forum/windows_7-security-winsec/some-malware-has-violated-windows-policy-with/6a5b097f-dbac-4240-acbf-83dad6ccebc1 where the user immediately thought of malware.

Comments
Display comments as Linear | Threaded
Anonymous on :
Found this directory on my PC and immediately thought it was malware as well. Wow.
Maciej on :
Today I also found it in my backup log. Immediately thought of some virus...
John Deere on :
I also found this today. Thought it was cheap-made virus lol.
Anonymous on :
Almost 6 years later and I just found that folder - assumed it was malware. Microsoft never fails to disappoint I suppose. Thanks for the great info!
MS on :
Making some cleaning after scammers breach of my family member PC, I was pretty sure it is some kind of payload left by them